Table of Contents
Introduction: Cloud Security
Cloud security refers to the set of policies, technologies, and practices designed to protect data, applications, and infrastructure in cloud computing environments. With the increasing adoption of cloud computing, ensuring the security of cloud-based assets has become a critical concern for organizations of all sizes and industries.
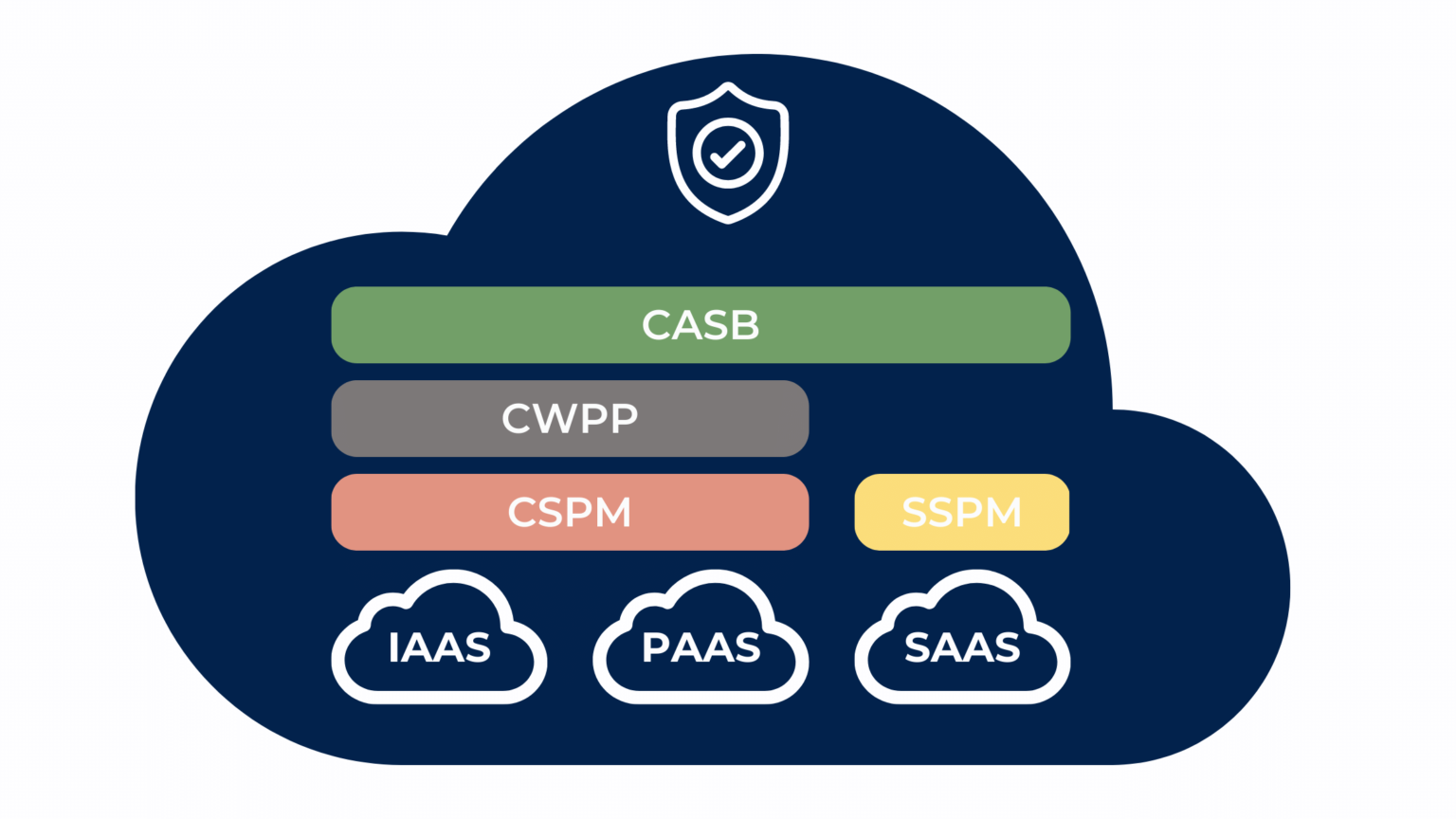
To address this concern, a variety of cloud security solutions have emerged, each designed to address different aspects of cloud security. The four primary types of cloud security solutions are CSPM (Cloud Security Posture Management), SSPM (Cloud Security and Compliance Monitoring), CASB (Cloud Access Security Broker), and CWPP (Cloud Workload Protection Platform).
While no single cloud security solution can protect an organization from all threats, it is important to implement a comprehensive cloud security strategy that includes a variety of solutions.
CSPM (Cloud Security Posture Management)
CSPM Meaning
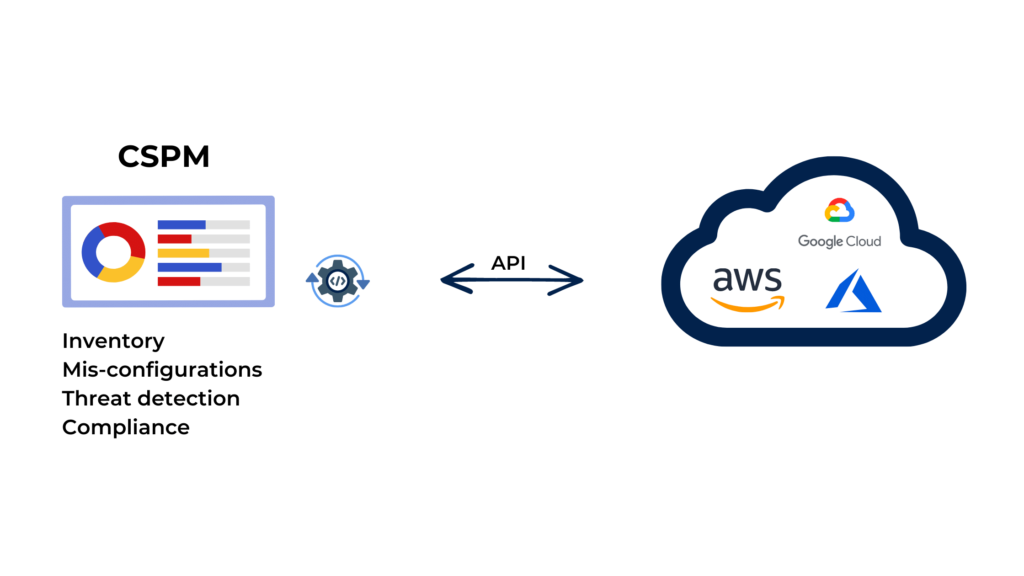
Cloud Security Posture Management (CSPM) is a security solution -often a cloud service- that helps identify and remediate security misconfigurations in cloud environments. Misconfigurations are one of the leading causes of cloud security breaches.
CSPM replaces the long process of manual audits, hence achieving a continuous monitoring and detection of risks. It can be considered as vulnerability management for cloud.
Benefits of using CSPM
Some of the benefits of using CSPM include:
- Reduced risk of security breaches: CSPM tools can identify and help to remediate security misconfigurations, and risks associated with OS versions and libraries of platforms running in the cloud which can help reduce the risk of security breaches.
- Improved cloud compliance: CSPM tools can also be used to continuously audit cloud environments against the controls of standards and industry regulations identifying compliance gap analysis.
- Increased visibility: CSPM tools provide greater visibility into cloud environments by clearly identifying assets and interconnections, which help identifying and addressing security risks more quickly.
- Automation: CSPM tools automate the process of monitoring and managing cloud security posture, freeing up IT resources and reducing the risk of human error.
- Cost Savings: CSPM can also be used to identify and eliminate unnecessary cloud resources, reducing costs and improving efficiency.
CSPM security is considered part of risk management and of the preventives security services every company using the cloud needs to have in order to reduce risk exposure. Every company that manages its cloud tenant, should have some kind of CSPM wether manually done or automated via a CSPM vendor tool.
CSPM Vendors
AWS CSPM is implemented in AWS Security Hub, Microsoft has Defender Cloud CSPM and Google Cloud has a similar implementation in Security Command Center.
Traditional Cybersecurity vendors also have their own CSPM tools as part of their threat detection platforms. There are also open source and script based solutions that can help identify threats in cloud configurations and map them to standards compliance.
Notable CSPM tools usually do not require the installation of any agent and work by interconnecting the CSPM solution to the cloud via API. A global reader access is generally required.
Use cases for CSPM
CSPM can be used in a variety of use cases, including:
- Cloud compliance Monitoring: CSPM tools can be used to monitor compliance of cloud environment against standards and industry regulations, such as HIPAA, PCI DSS, and GDPR.
- Vulnerability Management: CSPM identifies vulnerabilities in cloud infrastructure and applications. This exercise is often followed by cloud hardening which helps reduce the risk of cyberattacks and data breaches.
- Configuration Management: CSPM tools monitor cloud resources and services to ensure that they are configured securely and in accordance with best practices.
- Incident Response: Identify is the first phase of the NIST framework and hence CSPM can be used to generate an inventory of the monitored assets and understand their risk in order to protect them accordingly.
- Auditing: CSPM tools can be used to audit cloud environments for compliance and security issues.
- Risk management: CSPM tools can be used to assess the risk of cloud environments and identify areas where risk can be reduced.
SSPM (SaaS Security Posture Management)
SSPM Meaning
Software-as-a-Service (SaaS) security posture management (SSPM) is a cloud security service that helps identify and remediate security misconfigurations in SaaS applications. Misconfigurations are one of the leading causes of security breaches in SaaS applications, and SSPM tools can reduce their risk exposure.
Benefits of using SSPM
Notable SSPM vendors include Microsoft and their SSPM security software can be used with SaaS applications like Microsoft Office 365, Salesforce, GitHub or ServiceNow. It will examine the configuration of these services and suggest a list of improvements in order to enhance the security posture.
SaaS configuration checks can also be implemented manually using a script based approach, but SSPM will help automate the manual process and have it continuously run to identify new risks and monitor existing ones. This phase should always be followed by a cloud hardening exercise.
There are many benefits to using SSPM, including:
- Reduced risk of security breaches: SSPM tools identify security misconfigurations and suggest remediations, which can help reduce the risk of security breaches.
- Improved compliance: SSPM help ensure that SaaS applications are compliant with industry regulations.
- Increased visibility: SSPM provide greater visibility into SaaS applications, which can help identify and address security risks more quickly.
Use cases for SSPM
SSMP can be used in a variety of use cases, including:
- Compliance: SSPM tools can help organizations ensure that their SaaS applications are compliant with industry regulations, such as HIPAA, PCI DSS, and GDPR.
- Security: SSPM tools can help organizations identify and remediate security misconfigurations, which can help reduce the risk of security breaches.
- Auditing: SSPM tools can be used to audit SaaS applications for cloud compliance and security issues.
- Risk management: SSPM tools can be used to assess the risk of SaaS applications and identify areas where risk can be reduced.
CASB (Cloud Access Security Broker)
CASB Meaning
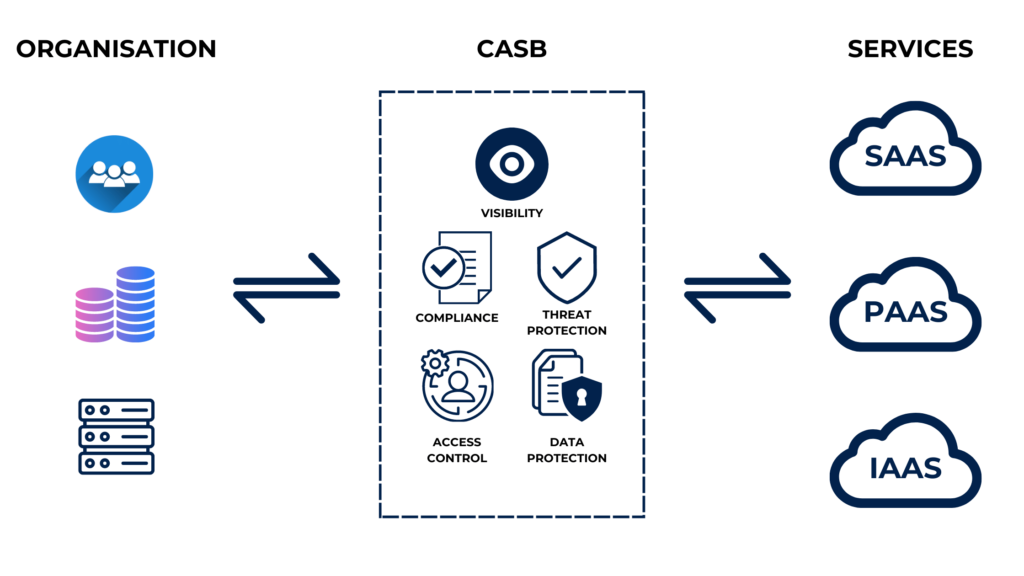
A cloud access security broker (CASB) is a security solution that controls and monitors access to cloud resources. CASB tools are designed to prevent unauthorized access to cloud resources, as well as track and audit user activity.
CASB solutions are implemented by intercepting access between users or devices and cloud services and will require API access to the cloud services in order to control the access.
Benefits of using CASB
There are many benefits to using CASB cloud security, including:
- Reduced risk of security breaches: CASB software can help prevent unauthorized access to cloud resources, which can help reduce the risk of security breaches.
- Improved compliance: CASB software can help ensure that cloud usage is compliant with industry regulations.
- Increased visibility: CASB provides visibility into cloud usage and activity. It also monitors data access and movement. This helps detect anomalies, risky behavior, and identify security gaps in cloud environments.
- Data Protection: CASB helps protect cloud-based data by enforcing data loss prevention policies, encryption, and access controls. It can also monitor and block unauthorized access to data from unmanaged or compromised devices.
- Threat Protection: CASB provides threat protection by detecting and blocking malware, phishing attacks, and other threats in real-time. It can also provide automated incident response and remediation.
- Control: CASB provides control over cloud usage and activity, enabling organizations to enforce policies, manage access, and prevent unauthorized use of cloud resources and applications.
Use cases for CASB
CASB tools can be used in a variety of use cases, including:
- Shadow IT discovery: CASB solutions can identify cloud applications and services used by employees outside of IT’s purview, enabling organizations to better manage the risks associated with these unsanctioned applications.
- Data loss prevention (DLP): CASB solutions can identify sensitive data stored in cloud environments and prevent it from being accessed or shared inappropriately.
- Security: CASB tools can help organizations prevent unauthorized access to cloud resources, as well as track and audit user activity.
- Auditing: CASB tools can be used to audit cloud usage for compliance and security issues.
- Cloud governance: CASB solutions can provide visibility into cloud usage and spending, enabling organizations to better manage cloud resources and optimize costs.
- Risk management: CASB tools can be used to assess the risk of cloud usage and identify areas where risk can be reduced.
CWPP (Cloud Workload Protection Platform)
CWPP meaning
A Cloud Workload Protection Platform (CWPP) is a security solution that helps organizations protect their cloud workloads from threats. CWPP tools can help organizations detect and prevent malware, ransomware, and other threats.
CWPP is for cloud services what EDR is for virtual machines or endpoints. Most CWPP vendors implement CWPP cloud security by installing a sensor in the cloud environment that will have enough rights to detect and prevent threats from happening within the cloud environment.
The CWPP sensor could be a container installed in a Kubernetes cluster and monitoring processes and traffic for malicious behavior. Like any other security service, incidents detected by CWPP should be treated within a Security Operations Center (SOC).
Benefits of using CWPP
There are many benefits to using a CWPP, including:
- Reduced risk of security breaches: CWPP tools can help organizations detect and prevent malware, ransomware, and other threats, which can help reduce the risk of security breaches.
- Improved compliance: CWPP tools can help organizations ensure that their cloud workloads are compliant with industry regulations.
- Increased visibility: CWPP tools can provide organizations with greater visibility into their cloud workloads, which can help them identify and address security risks more quickly.
Use cases for CWPP
CWPP security can be used in a variety of use cases, including:
- Cloud compliance: CWPP tools can help ensure that cloud workloads are compliant with industry regulations, such as HIPAA, PCI DSS, and GDPR.
- Auditing: CWPP tools can be used to audit cloud workloads for compliance and security issues.
- Risk management: CWPP tools can be used to assess the risk of cloud workloads and identify areas where risk can be reduced.
- Threat detection and response: CWPP solutions can detect a range of cyber threats, including malware, phishing attacks, and data exfiltration attempts, and respond to them in real-time.
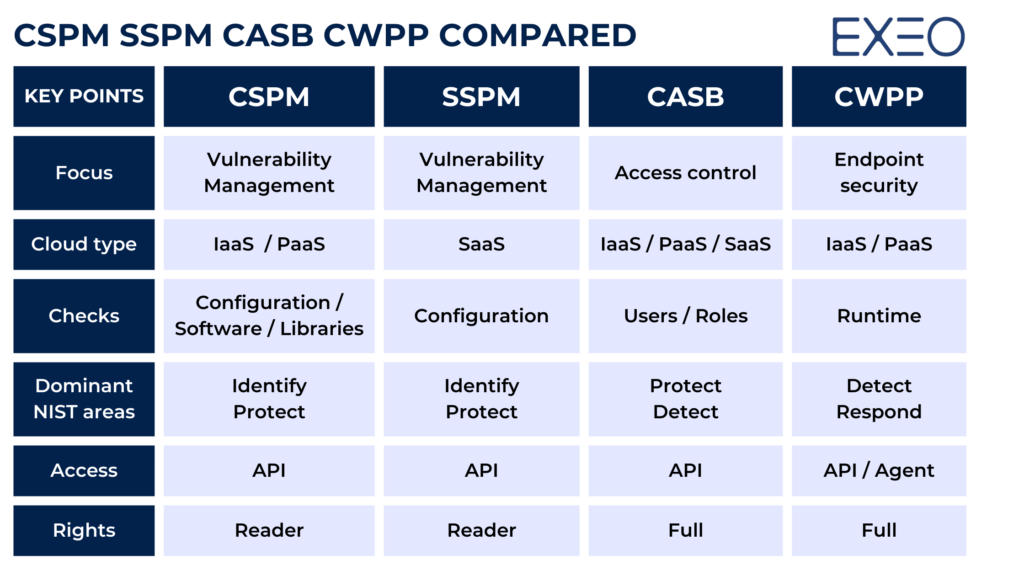
Key differences between CSPM, SSPM, CASB and CWPP
The cloud security solutions CSPM, SSPM, CASB and CWPP are different aspects of cloud security that stack up with the other corporate security layers and controls in order to complement each other and complete the overall security practice.
It is important to understand the differences between these different cloud security solutions in order to choose the right solution for your organization’s needs. For example, if your organization is concerned about data security, you may want to consider a CASB or CWPP. If your organization is concerned about security vulnerabilities and misconfigurations, you may want to consider a CSPM or SSPM.
Here is a small table describing the major differences.
How to choose the right solution for your organization
There are many cloud security solutions to choose from, but it is important to keep the focus on security practice before looking for a solution. Here is the approach we are suggesting:
If you are using a SaaS solution
Like Microsoft Office 365 or Salesforce, then you need to implement SSPM. This doesn’t mean that you need to procure a solution, but you need to audit the configuration of your cloud tenant at least twice a year in order to detect misconfigurations or vulnerabilities.
If you have applications running in the cloud (IaaS or Paas)
and you are operating a cloud tenant (such as AWS, Google Cloud or Azure), then you need to implement CSPM in order to identify threats coming from misconfigurations or versions of software
If you apps are running on micro-services or containers
It means that the nodes these containers are running on are not protected by any cybersecurity agent (since you don’t have control on them), hence you need to implement a CWPP solution in order to detect malicious behaviour and block them.
If you have a high number of users accessing apps on heterogenous cloud
Then you might want to consider CASB in order to centralise user access policies and propagate access rules across all the environments.
Future trends in cloud security
The future of cloud security is constantly evolving, but there are a few key trends that are likely to continue in the years to come.
- Increased adoption of multi-cloud and hybrid cloud environments. As cloud computing adoptions continues to grow, clients will increasingly adopt multi-cloud and hybrid cloud environments. This means that they will need to manage security across multiple cloud providers and on-premises environments.
- Increased focus on data security. As clients store more data in the cloud, they will need to focus on data security. This includes protecting data from unauthorized access, disclosure, modification, or destruction.
- Increased use of artificial intelligence (AI) and machine learning (ML) for security. AI and ML are being increasingly used for security purposes. For example, AI can be used to detect anomalies in network traffic that may indicate a security breach. ML can be used to learn from past security incidents and improve the accuracy of security predictions.
- Increased focus on security awareness and training. As clients adopt cloud computing, the weakest link in the security chain, remains the user. Hence it is important to ensure that employees are aware of the security risks associated with cloud. This includes providing employees with security awareness training and ensuring that they understand the security policies and procedures of the organization.
Running in the cloud has many advantages, but because you are sharing a public infrastructure extra care needs to be given to the design and implementation of security controls over the preventive, detective and response services. Exeo can guide its client to securely operate from the cloud through its managed security services.