cybersecurity
Managed Security Services Provider (MSSP)
Protect User, Apps and Data
Managed Security Services 24/7 for every business
Exeo’s Managed Security Security Service is delivered by a managed security operations center, which is also called SOC as a service -Security Operations Center as a Service (SOCaaS).
This service makes it possible for clients to onboard an on-demand team of security specialists in order to identify, secure, monitor and respond to incidents in an effective manner and prevent cyber attacks. It also avoids clients the hassle and complexity of building this expertise in-house while relying on a trusted, recognised, and certified managed security services provider like Exeo.
A Managed Security Service Provider (MSSP) like Exeo, uses a combination of technology, processes, and expertise mobilized for a defined objective. The scope and pricing of this mission are defined by the device or by the protected user.
Hence the client, builds this capability overnight and adopts it in a managed way. Clients also benefit from the immediate availability of state-of-the-art protection, detection & response technology delivered by advanced security engineers operating 24/7 to secure their business, users, data, and apps.
Why Do You Need an MSSP?
Identity & Access Management
It all starts with the identity, which must be harmonious and propagated to all environments: on-premises, hosted, or cloud. We support our clients in the development of a unified access control strategy for all their essential resources.
Benefits of Managed Security Services
Risk Management
Clearly identify all the managed assets, continuously assess their risk level by setting a score and try to reduce it. Vulnerability management will also help reduce the risks of those assets.
Strengthening
Strengthening the security of workstations and servers by detecting and stopping attacks through Managed Detection & Response (EDR / MDR).
Detection and response
Early detect security incidents through advanced analysis and monitoring using technologies such as SIEM (Security information and event management) or UEBA (User and Entity Behavior Analytics)
Service Protection
Protect internet corporate services like email or client facing services like web apps, mobile apps or APIs.
Expertise & Compliance
Our team of experts has extensive knowledge and experience in cybersecurity. Being compliant, we also help organizations meet regulatory requirements and adhere to industry standards.
Proactive Approach
Managed security services use a proactive approach to security, anticipating and mitigating potential threats before they can cause damage.
How EXEO can help secure your business as an MSSP
Managed Security Service Providers to make the Cloud Safe for Everyone
Cloud & Infrastructure Hardening
In order to minimize the surface of attacks, it is important to harden infrastructure and cloud resource configurations. Our services include a hardening of the security of the managed infrastructures.

Managed security services providers to protect your email
Managed Email Protection
Email is today the vector of choice for malware and ransomware, the first step we take towards our customers is to secure their email channels and eliminate the threat by protecting this channel with advanced technologies.
More details here our managed email security services.


PROTECT
Managed WAAP - Web Application & API Protection
More details in the following page on our managed WAF service.
PROTECT
Managed Firewall and SD-WAN
We also provide a managed security framework by teaming up with Arista Edge Threat Management (previously Untangle) to provide a managed firewall and managed SD-WAN.
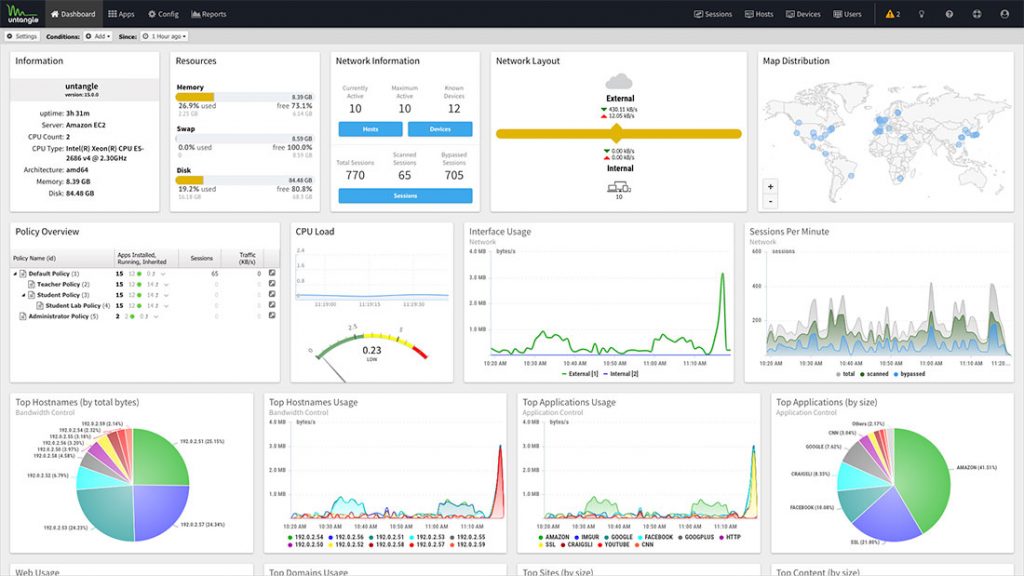
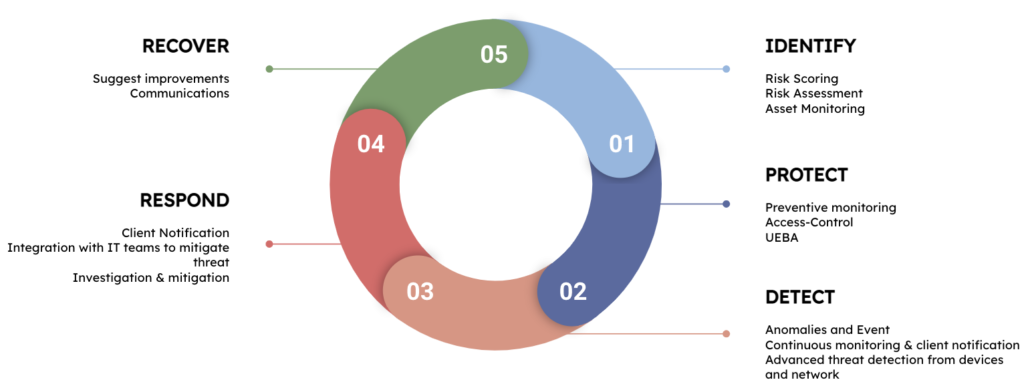
THREAT DETECTION, RESPONSE & RECOVERY
Managed SOC
It implements detection and response services based on the NIST (National Institute of Standards and Technology) methodology.
The services are:
- Risk analysis;
Protection of systems and maintenance in optimized condition; - Incident detection;
- Attack Isolation;
- Response to incidents remotely or on-site;
- Recovery of the initial configuration;
Securing and hardening of the installation;

Windows, Mac and Linux platforms are supported and pricing is per device per month.

Lear more about MDR service.
THREAT DETECTION - MDR
Managed Endpoint Detection & Response (MDR)
Exeo is a cybersecurity company and, specifically, a managed security services provider that uses EDR and XDR solutions to secure workstations, servers, and Cloud environments. This service is provided as part of managed security services and includes the service and software suite.
Exeo monitors the security of cloud, servers and on-premises endpoints by detecting threats and reacting to them immediately.
Managed detection and response services start with endpoint detection, and response (EDR), data from this platform is supplemented with data with telemetry from the network, identity, cloud (XDR), and other sources to produce high-fidelity detections, conduct investigations, provide remote incident response support, enable security automation, and launch threat hunts to identify adversaries.
THREAT DETECTION
Managed SIEM
As a managed services provider, we leverage the power of our analysis and threat detection software to monitor our customers’ resources 24x7x365.
Additionally, we use advanced techniques such as User Entity Behavior Analytics (UEBA) to categorize and remediate user risk.
Within our managed service, the Managed SIEM service is optionally integrated with the Managed Detection & Response and Vulnerability Management service.
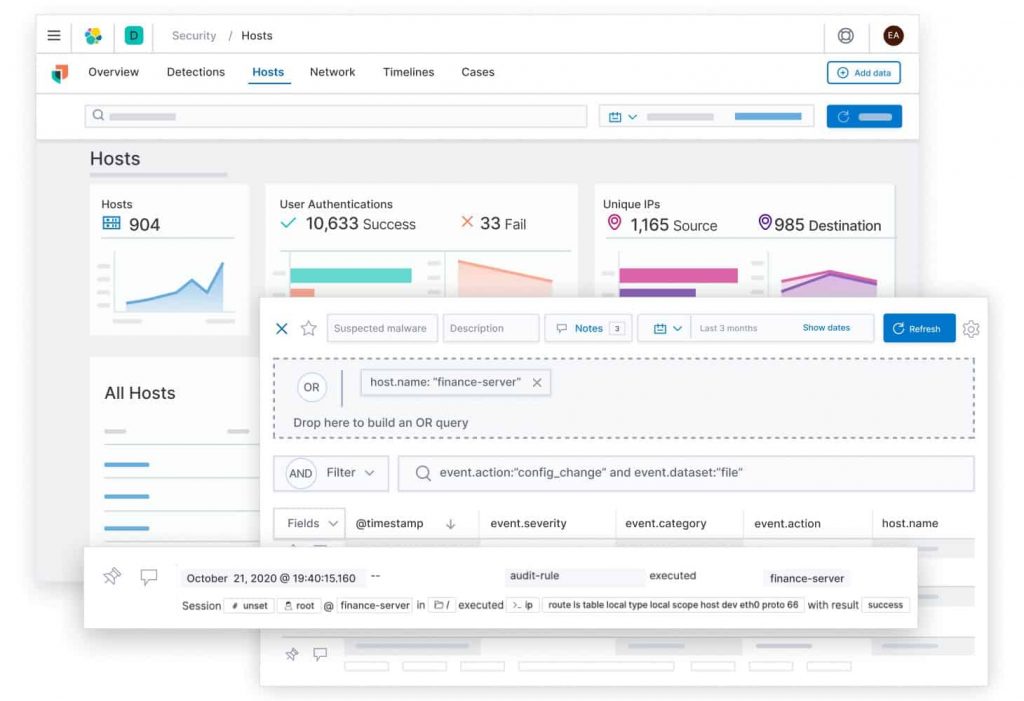
How is EXEO different from other Managed Security Service providers?
Exeo understands that outsourcing managed security services is a critical decision made by clients, for that reason, it has built an offering that makes it uniquely positioned to service its clients.
1.Certification and Accreditation
The managed security service consists of cybersecurity professionals trained to detect and respond to incidents. Three types of specialists are part of the managed security service:
- Analysts will triage events and escalate potential incidents that require advanced investigation;
- The specialists examine you on the identified incidents and initiate the response process;
- The experts will intervene on advanced incidents and perform cyber forensics when necessary.
Furthermore, as a managed security service provider (MSSP) Exeo is certified with the following standards: ISO 27001, ISO 27017, ISO 27701, SOC2 Type 2 and Expert Cyber. These certifications make Exeo one of the top cybersecurity services companies.
2.Transparency and Accountability
The managed security services operate in full transparency, and clients get access to the cybersecurity management tools that Exeo uses in order to detect and respond to threats. Secure access is created for selected Client personnel that has the capability to access the Cybersecurity platforms used by Exeo.
3.Advanced Technology Capability
The MSSP is trained and manages workloads located in multi-cloud environments for clients around the world. Thousands of users and resources are currently monitored and protected, including resources located on-premise in Microsoft 365, Google Workspace, Azure, Google Cloud Platform, AWS or Oracle Cloud Infrastructure.
Hence, it is up to date with the latest technology environments, it is using latest generation tools from the top cybersecurity providers and is capable of securing new generations of IT workloads and detecting threats in non-usual infrastructures. Exeo is a managed security service provider which is capable of assessing vulnerabilities in cloud environments while at the same time hardening and remediating to those vulnerabilities.
THREAT DETECTION
Vulnerability Management
Continuous vulnerability detection and risk assessment of our customers’ critical assets helps us prevent attacks and keep them secure.
In addition, this vulnerability management is integrated with our Managed SIEM service in order to better control the scope of potential threats.
Managed Security Services Provider FAQ
Computer security is a multi-step process.
To prevent ransomware, the most important thing is to implement a next-generation security agent (EDR – Endpoint Detection & Response, XDR – Extended Detection & Response) on workstations and servers, capable of detecting malicious behavior. But it is above all essential to combine this technique with a detection and response service (MDR, Managed Detection & Response) consisting of experts capable of responding to incidents and countering all types of attacks.
Microsoft 365 filters aren’t 100% effective.
Even Microsoft Defender for Microsoft 365 misses a fair number of threats. It is recommended to implement additional security to Microsoft 365 security with an email security service.
This service will make it possible to detect and prevent attacks such as ransomware, identity theft (impersonation) or cyber fraud.
Once a web or mobile application is published, everyone has access to it.
However, the risks are numerous, they can come from the programming platform, the servers or the quality of the code. A Web application Firewall (WAF) will intercept all requests intended for the application and inspect them to filter out malicious requests.
In addition, a Web application Firewall (WAF) will also allow us to apply effective and fast rules to pages based on different criteria such as user geolocation.
Cloudflare is a recommended solution because it couples security with the CDN (Content Delivery Network) which will speed up service to users and relieve congestion on the application’s servers.
Contact us
What can EXEO do for your business?
We believe that digitisation is not an end by itself, but a mean to get to a more productive and efficient business operation that supports every organisation’s objectives.