Table
Cloud hardening: Definition
The hardening limits the vulnerability of the cloud facing the attacks. It requires specific rules for system configuration and a whole lot of good practices.
For about ten years, enterprises migrate their computer systems to the cloud. Henceforth, 93% among them are using it.
Facing the attacks, the cloud isn’t infallible. The massive recourse to teleworking has weakened the IT security of the organizations. In 2020, at the height of the pandemic, 47% of the enterprises have rung up an increase in cyberattacks.
The users are 99% responsible for the cloud cybersecurity breach. Adopting a “Cloud hardening” approach contributes to creating a secure IT environment.
What are the practices to adopt: Secure your cloud with our 5 recommendations.
Key figures: The Cybersecurity should be improved
- About 85% of the cybersecurity violations are caused by human errors (Verizon);
- The cloud computing attacks have increased by 630% in 2020, in comparison with 2019 (McAfee);
- 4 SMEs over 10 (42%) have already been subject to one or several IT attacks or attempted attacks. (L’Usine Nouvelle);
- More than 21% of all the enterprise files are opened to everyone. (CLUSIF)
Step 0: Cloud Cybersecurity Risks evaluation
Before starting your hardening exercise, it is best to have your cloud tenant(s) risk assessed.
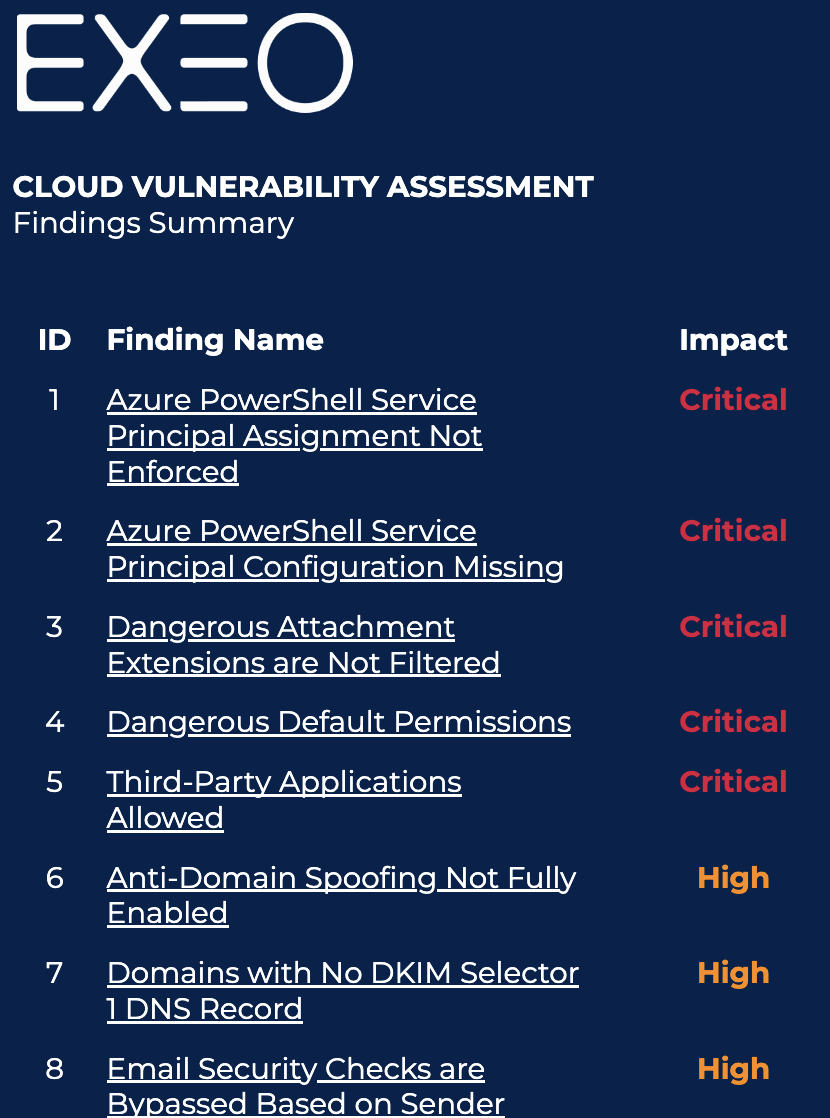
This assessment takes the form of a cloud vulnerability audit which will allow you to understand the exposure of your environment to threats and at all levels of cloud computing (compute, storage, network, security, IAM, etc.) .
The results of this assessment will help you better build the cloud hardening roadmap. Being certified cloud cybersecurity professionals, Exeo can support you in this exercise with its cloud security risk evaluation.
1. Harden the tenant and Secure the cloud management console
A cloud service subscription requires the supplier to use a management console. This tool, sometimes also called cloud control panel, is specific to each organization. It allows to perform many adjustments on the client side such as:
- Managing the users’ accounts.
- Controlling the access rights.
- Configuring the cloud services.
- Repairing (detection, identification and problem resolution).
- Supervising the users’ activity.
- Invoicing, etc.
The cloud management consoles are regularly targeted by hackers. The most striking example is probably the one of the code host Code Spaces, which the diversion of an administration account from its AWS console has led to the bankruptcy of the whole enterprise.
Without a correct administration, the cloud control panels constitute weaknesses and major vulnerabilities of the organization IT system. It is up to the enterprises to control carefully and restrict the access rights and the privileges on these tools.
The best security practices applicable to the cloud management console are built on a Zero Trust approach. They are mainly consisted of:
- The inventory of the users’ accounts by adapting their rights;
- Multi-factor authentication (MFA);
- The access restrictions to Applications Programming Interfaces API for reliable sources and IP addresses only;
- The logging across the entire cloud environment.
Depending on the type of Cloud provider there are a series of Cloud hardening controls which should be implemented on each tenant and on each cloud service. These controls are based on best practice and vendor recommendations. To understand which control needs to be hardened in each specific case, Exeo has quick cloud security assessment (Cloud Vulnerability Management) that would outline the risks in the cloud and list the controls by severity. More on this topic in this article.
2. Secure the identities: the least privilege policy
According to the Top 10 document of the Open Web Application Security Project (OWASP[4]) itemizing the most critical security risks, the defective access or authentication controls are responsible for at least 4 of 10 main vulnerabilities hanging over the organizations.
The principle of least privilege (PoLP) is the inevitable cybersecurity practice for access protection. It is a fundamental component of the Zero Trust architecture which stipulates that the individual should only have the minimum privileges necessary to complete a specific task.
In practice, this principle of least privilege doesn’t only apply to individuals, but also to equipment, applications, processes, services or to networks, as well, that can have access to cloud resources. When it comes to securing the identities, all these elements should be considered as active entities with access rights and clearly defined privileges.
In order to implement the principle of least privilege, enterprises should follow these good practices:
- Delete all the inactive accounts;
- Carry out regular audits to reassess accounts and privileges;
- Limit the “privileged” account numbers, especially those of the administrators;
- Check the logs frequently and monitor all authentications and authorizations on critical systems;
- Set up time-limited privileges;
- Implement the related security principles, particularly the segregation of the tasks and the users’ profiles according to the actions to be performed.
At the same time, reinforced identification rules such as the Single sign-on (SSO) and strict password policies should be carried out.
3. Protect the cloud resources: Managed Detection & Response (MDR)
By definition, the cloud allows the information to be transferred from and to accessible resources via the Internet. Therefore, it is essential to have the use of a solid protection on the cloud allotted resources. These Endpoint Protection (EPP) agents combine the firewall functionalities, web filtering, antivirus, anti-malware, etc.
With the intensification and sophistication of the cyber threats, the enterprises should also evolve their defenses in order to adapt. Tools such as the Endpoint Detection and Response (EDR) allows them to reinforce their security, including when they access the cloud.
The EDR solutions consist of agents and sensors monitoring the terminals. These platforms collect and send behavioral data to a centralized intelligence for analysis.
The MDR (Managed Detection and Response) functions in a similar way, except that the analysis and the responses to cyber threats are entrusted to teams of specialists such as EXEO analysts.
At EXEO, hence, we deliver managed security services that integrate the managed endpoint protection within our Cloud Hardening offers.
We provide an MDR and Next Generation MSIEM (Managed Security Information and Event Management) service in order to:
- Detect the threats;
- Identify the vulnerabilities;
- Guarantee the security of the IT resources.
Definition of MDR according to Gartner:
According to Gartner: “Managed detection and response services provide customers with remotely delivered modern security operations center (MSOC) functions. These functions allow organizations to rapidly detect, analyze, investigate and actively respond through threat mitigation and containment.”
4. Protect the data: the cloud to cloud backup
The backups are inescapable security elements that allow faster activity recoveries in case of incidents and limit data losses and compromises.
In this field, a security practice is to appeal to the cloud to cloud backup (C2C). This approach consists of archiving the data of a cloud service to another cloud service. It has the same objective as the regular backup, but it includes additional advantages such as:
- A better accessibility since the saved data is available from everywhere.
- A reinforced protection facing ransomware attacks, since the data is not stored on the internal network.
- A greater coverage, because the C2C backups protect the user against numerous cases of data compromise.
On the other hand, the C2C backups could be complicated to set up. The organizations should clearly make the inventory of the data they are using and its interaction within the different cloud services. This follow-up ensures that the latest updated information is well saved and accessible in case of incident.
For further simplicity and efficiency of the cloud backups, EXEO offers a managed backup service based on Acronis cloud. We guarantee to our clients a daily monitoring of the data backup process, particularly with:
- Encryption at the source of the data.
- A 99.995% availability.
- Guaranteed and fast restorations.
5. Set up a 24/7 monitoring service
Monitoring the cloud environment and the whole IT infrastructure is one of the pillars of cybersecurity policies. The cyber threats are in continuous evolution; new security breaches could be created or exploited at any time by cyber attackers (the zero-days vulnerabilities).
Man-made vulnerabilities could also thwart the most advanced protection devices.
The continuous surveillance of the accesses, authorizations and uses is moreover one of the fundamentals of Zero Trust approach.
At cloud level, these good practices of surveillance include:
- Knowledge of the cloud providers’ commitments in order to determine the part of the security that is incumbent upon them to ensure and the other part that will be the client’s responsibility.
- Monitoring the security metrics to detect the threats and react.
- Observation of behavior in each layer of the infrastructure.
- Taking into account the user experience data.
- Automation of monitoring and reaction tools.
Numbers to be remembered:
“90% of the enterprises using a public cloud that fails to define an appropriate security protocol will face at least one sensitive data leak by 2024.”According to Gartner
This continuous monitoring is automated, but it requires human intervention in order to continuously assess the risks and take the appropriate measures.
At EXEO, we offer a totally managed cloud monitoring service.
We combine these industry-leading security credentials with threat analysis and detection software to keep our customers safe.
Why should you have confidence in EXEO to reinforce your Cloud security?
EXEO offers a more affordable and agile IT. Our professionals are already working with thousands of cloud users, spread over four continents. Our mission: to help our clients adopt cloud services in the best security conditions.
The EXEO expertise in 3 words:
- Accelerate your process, via an Agile IT approach.
- Protect, with concrete actions in favor of your cloud hardening.
- Optimize through an increased use of digital technologies and process automation.
The 3 key points to remember
- The cloud cybersecurity responsibility
It is the concern of both the service provider and the client. Most of the flaws are the consequence of the client missing practices.
- To adopt a security approach…
Operating the cloud services in their full potential requires a specific security approach. The multiplication of the possible points of access for attacks implies constant monitoring.
- … with the good partner
However, the security protocol set up for the cloud clients requires time and internal solid resources. In order to safely operate all the cloud service potential, EXEO has the necessary skills to accompany you in your cloud hardening process.
contacT US
ASK FOR an EValuation on your CLOUD SECURITY