We hear about high profile security breaches frequently. Most of these breaches exploit the system login credentials of end users to get into the company’s network. Therefor, Leading organizations are recognizing this and are beginning to focus on a better secure end user identities.
The requirement of enforcing an additional authentication method is at all time high, therefore MFA became the most popular technology.
These additional factors of authentication require the user to provide something that only the user knows, has and is.
To enable MFA for desktop logon, We use Google Authenticator as OTP Token provider.
How does Google Authenticator algorithm:
Google Authenticator is a mobile app that implements two-step verification. It uses the time based one-time password algorithm (TOTP) and HMAC-based one-time password algorithm (HOTP) for authenticating user logons.
Click here to download Google Authenticator for Apple IOS
Click here to download Google Authenticator for Andoid OS
We seek adding a 2FA security layer to our windows Logon, hence the need to link Google Authenticator to the Authentication tool.
Firstly, we need to scan a unique QR Code provided by the tool is needed.

Secondly, Google Authenticator home page will display the newly scanned account with its unique token.
The same App can support unlimited number of accounts .
The account you enforced 2FA for won’t be able to logon to his Desktop without using a secure Token provided by Google Authenticator on his mobile, However, the user can logon using a set of predefined secret questions in case the App wasn’t available.
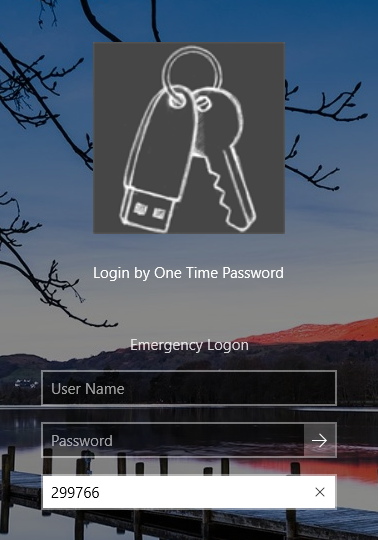
Two-factor authentication prevents hackers from targeting your account, many will simply move on and find easier accounts to break into. And should they target you, they’ll need more than just your password. In addition to your password, a hacker would also need to have your phone.
To find out more about adding Two-Factor Authentication to your organization infrastructure, contact our team.