Table of Contents
Securing sensitive data is a top priority as we navigate a significant digital transformation. Applications are increasingly distributed across private or public clouds built on shared infrastructure technologies.
While encrypting data at rest or in transit enhances confidentiality, data is often in clear text during processing, exposing it to potential interception by malicious actors, insider threats, or backdoors.
Confidential computing aims to protect data during processing, also known as data in use, a critical phase frequently overlooked in traditional security measures. This technology leverages a Trusted Execution Environment (TEE) to create a secure enclave, ensuring data remains encrypted not only during storage or transit but also while in use.
The Need for Confidential Computing
- Insider Threats: Employees or contractors might misuse their access privileges to read or manipulate sensitive data.
- Memory Dumps: Hackers can exploit vulnerabilities to capture sensitive data residing in a server’s memory.
- Malicious Hypervisor or Firmware: A compromised hypervisor or malicious firmware and backdoors can compromise the data being processed.
- Network-Based Attacks: Data could be intercepted or altered during transfer between virtual machines.
The Need for Confidential Computing in AI Applications
As AI applications proliferate, the data they process often remains exposed in memory, accessible to unauthorized entities through vulnerabilities. This exposure is particularly concerning where massive datasets, including personal and sensitive information, are processed and analyzed.
Confidential computing addresses this gap by using secure enclaves. These enclaves provide a protected memory space where data can be processed without exposure to the rest of the system, crucial for maintaining the confidentiality and integrity of the information being analyzed by AI algorithms. This security is indispensable in applications ranging from personalized medicine to financial services, where the protection of data directly impacts trust and compliance.
Moreover, the use of confidential computing in AI is not just about security; it’s also about enabling more innovation. By ensuring data can be processed securely, organizations are more willing to leverage AI for more complex, sensitive tasks without fearing data breaches. This encouragement of broader, more confident AI deployment can drive significant advancements across sectors.
Understanding Confidential Computing
To effectively harness the power of confidential computing, it’s essential to understand its underlying principles. Here’s an overview of the key concepts and how they interact with your business data.
Key Concepts
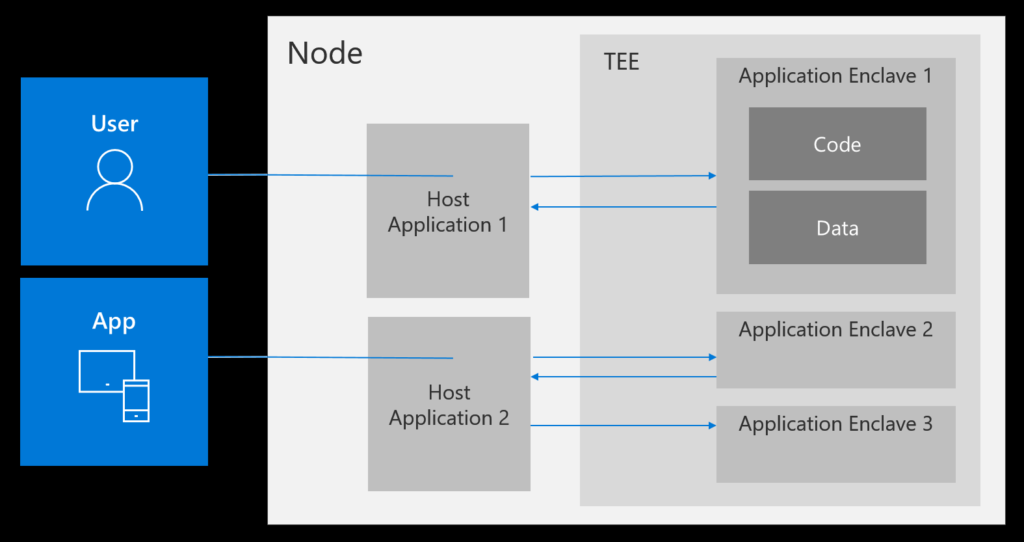
At its core, confidential computing uses a Trusted Execution Environment (TEE), which is a secure enclave of the processor. The TEE ensures that the data is encrypted and isolated from other processes. The TEE acts as a fortified vault, isolating the data it holds from the rest of the system, including the operating system and other applications.
This means that confidential computing provides a secure space where sensitive data can be processed without fear of exposure to internal or external threats. This is crucial when handling personal customer information, proprietary algorithms, or any data that offers you a competitive edge.
Of course, the protection of confidential computing extends across multiple scenarios, whether the data is used for everyday business operations or complex computations like machine learning models.
How Confidential Computing Works
You already know that the operation of confidential computing centers around the TEE. Here’s a simplified breakdown of how it works:
- Isolation: The TEE separates sensitive data and processing tasks from other parts of the system, reducing the risk of leaks or unauthorized access. This isolation ensures that even if a hacker gains access to the operating system or other processes, they can’t view the data inside the TEE.
- Encrypted Execution: While data is processed within the TEE, it remains encrypted and is only decrypted within the enclave itself. This means that any data leaving the enclave, whether for storage or further processing outside the TEE, remains encrypted. The application with authorized access can decrypt this data within the TEE, but it appears encrypted and inaccessible to any other parties operating on the system.
- Attestation: The TEE supports attestation mechanisms that certify to external systems and users that the secure enclave is operational and has not been tampered with. This certification is crucial for maintaining trust in the environment’s integrity, especially when processing highly sensitive information.
Benefits
With these key features, confidential computing provides a secure space for processing sensitive data like personal customer information, proprietary algorithms, or intellectual property. The protection extends to various use cases, whether the data is used in routine business operations or for more advanced tasks such as machine learning and data analytics.
By understanding these fundamental concepts, businesses can better leverage confidential computing to secure their data throughout its lifecycle and ensure compliance with stringent data protection standards.
Technologies Behind Confidential Computing
We’ve tried to simplify the process as much as we can. But still, different types of back-end technologies go into achieving the results of confidential computing.
Intel's TDX (Trust Domain Extensions)
Building on the foundation laid by Intel’s Software Guard Extensions (SGX), Intel has developed the Trust Domain Extensions (TDX) to enhance the security capabilities of virtual machines.
While SGX provided secure, isolated computation within smaller trusted execution environments, TDX extends these principles to virtualized environments, addressing larger-scale enterprise needs. TDX significantly reduces the attack surface accessible to the hypervisor by establishing more robust isolation and encrypting memory in virtual environments. This advancement ensures that even system administrators with higher-level access cannot view the encrypted data, thanks to elements such as SEAM (Secure Enclave Attestation Mechanism), EPT (Extended Page Tables), GPA (Guest Physical Addresses), and TME-MK (Total Memory Encryption-Multi-Key).
It also reflects Intel’s response to market demands where AMD has already made significant inroads. AMD introduced its Secure Encrypted Virtualization-Secure Nested Paging (SEV-SNP) technology in 2021, which offers similar capabilities. Thus, Intel’s TDX can be seen as part of its effort to align with or exceed industry standards set by competitors like AMD.
AMD's SEV-SNP (Secure Encrypted Virtualization-Secure Nested Paging)
AMD’s SEV-SNP builds on the Secure Encrypted Virtualization (SEV) technology by adding stronger memory integrity protections. This additional protection measure helps prevent sophisticated attacks, such as replay attacks where old memory states are maliciously reinstated.
SEV-SNP works by encrypting and isolating the memory of virtual machines, making them invisible to the host system and any other virtual machines running on the same hardware.
One of the best outcomes of this capability is that your sensitive business data remains protected during both execution and rest.
AMD introduced SEV-SNP with its EPYC 7003 series processors, also known as “Milan,” which are part of the third generation of EPYC server processors. These processors were launched on March 15, 2021.
5 Questions about Secure Encrypted Virtualization (SEV) from the AMD Youtube Channel
IBM's Secure Execution for Linux
IBM’s Secure Execution for Linux is a security feature designed for IBM Z and LinuxONE platforms. As a result, it creates a highly secure virtual machine environment. This technology uses hardware-based encryption to create isolated TEEs for running sensitive applications.
The security measures built into the system ensure that only authorized code can access the protected data. This makes Secure Execution ideal for highly regulated industries like financial services and healthcare.
Secure Execution for Linux also allows enterprises to leverage the benefits of cloud and hybrid environments while ensuring the confidentiality and integrity of their critical workloads.
Google Asylo
Google’s Asylo is an open-source framework for confidential computing that enables developers to build applications that can run in TEEs. Asylo provides a variety of tools and libraries that simplify the development of applications that require strict data confidentiality.
By abstracting some of the complexities associated with creating and managing secure enclaves, Asylo makes it accessible for more businesses to implement confidential computing in their operations, at somewhat reduced costs.
The good thing about this framework is that it supports various backend technologies, including Intel SGX and AMD SEV. It means the framework works for different hardware settings.
Microsoft's Azure Confidential Computing
Last but not least, Azure Confidential Computing by Microsoft allows data processing in secure enclaves on the Azure cloud platform. This service extends the security capabilities of confidential computing to a wide range of applications. From blockchain to AI, nothing is off-limits!
From what we can tell, Azure’s approach is unique as it provides a comprehensive suite of tools and services that support the implementation of confidential computing. Whether it’s the initial design of applications or their deployment, everything happens in a secure environment.
AWS Nitro Enclaves
AWS Nitro Enclaves provides isolated compute environments to process highly sensitive data securely on AWS EC2 instances. Nitro Enclaves helps ensure that the data being processed is isolated from the main EC2 instance, minimizing the risk of external access or interference.
Google Cloud Confidential VMs
Google Cloud offers Confidential VMs that allow data to be encrypted not only at rest and in transit but also while in use. Utilizing the capabilities of Secure Encrypted Virtualization provided by AMD’s hardware, these VMs provide an additional layer of data protection, ensuring that data is inaccessible to cloud administrators and other cloud services without permission.
Benefits of Confidential Computing
- Enhanced Data Security: As confidential computing encrypts data in use, your sensitive information is protected against unauthorized access and leaks. It doesn’t matter if that data is on shared environments like the cloud servers.
- Compliance and Regulatory Assurance: This technology helps businesses meet strict data protection regulations such as GDPR and HIPAA by providing robust security measures that safeguard customer and patient information.
- Increased Customer Trust: As a business, you can strengthen trust with clients by protecting their sensitive data. It’s especially important for sectors like finance and healthcare where confidentiality is one of the core principles.
- Enabling Innovation: Confidential computing allows you to explore and implement new technologies without worrying about data breaches. You get to tinker with artificial intelligence and machine learning because your datasets remain confidential and secure throughout the processing phase.
- Competitive Advantage: Last but not least, you can differentiate your business in the crowded market by attracting customers who value privacy and security over anything else.
Confidential computing on AWS, Azure & GCP
The table compares the confidential computing features implemented at AWS, Azure and GCP.
| Feature | AWS Nitro Enclaves | Azure Confidential Computing | Google Cloud Confidential VMs |
|---|---|---|---|
| Key Components | EC2 instances, Nitro Enclaves | DCsv3-series, SGX-enabled hardware | N2D and C2D series, AMD SEV-enabled VMs |
| Hardware Security | Dedicated Nitro Hypervisor | Intel SGX enclaves, AMD SEV, TEE | AMD SEV, Hardware-based encryption |
| Supported Workloads | Data processing, machine learning, financial apps | Machine learning, data analytics, app dev | Data processing, machine learning, analytics |
| Encryption | Memory isolation, EBS encryption | In-use data encryption via Intel SGX | In-use data encryption via AMD SEV |
| Management Tools | AWS CLI, SDK, CloudFormation | Azure Portal, PowerShell, ARM templates | Google Cloud Console, gcloud, APIs |
| Networking | Isolated VPC | Virtual Network isolation | Virtual Network isolation |
| Compliance | HIPAA, GDPR, PCI DSS | HIPAA, GDPR, PCI DSS | HIPAA, GDPR, PCI DSS |
| Integration | AWS KMS, S3, Secrets Manager | Key Vault, Managed HSM, Disk encryption | Cloud KMS, IAM, Secret Manager |
| Cost | No additional charge for Nitro Enclaves | Premium for DCsv3-series instances | Premium for Confidential VM instances |
| Date of Release | 2020 | 2018 | 2020 |
Challenges and Limitations
While confidential computing is the future of data security, it presents some challenges and limitations as well. What are they, you ask?
- Complex Integration: Implementing confidential computing can be complex, particularly when integrating with existing IT systems. You might need specialized knowledge, or at least hire experts to deploy these technologies effectively.
- Performance Overhead: The additional security layers can introduce latency, potentially slowing down data processing speeds. If you mostly deal with time-sensitive applications, it should be an important consideration for you.
- Cost Implications: Setting up and maintaining the infrastructure for confidential computing can be costly, especially for small to medium-sized enterprises (SMEs).
- Limited Vendor Options: Older applications and systems may not be seamlessly compatible with the new confidential computing environments. Although upgrading IT infrastructure to support confidential computing is possible, it requires additional investment and strategic planning, which could be a barrier for some organizations.
- Technology Compatibility: Older applications and systems may not be compatible with confidential computing environments. You can still implement it but your IT infrastructure might need a refresh.Older applications and systems may not be seamlessly compatible with the new confidential computing environments. Although upgrading IT infrastructure to support confidential computing is possible, it requires additional investment and strategic planning, which could be a barrier for some organizations.
Future of Confidential Computing
Findings from the market study by Everest Group show the Confidential Computing market is projected to grow at a CAGR of 90%-95% to reach US$54 billion in 2026.
To us, the future of confidential computing looks promising as it becomes increasingly integral to business operations across various industries. As cloud technologies evolve and businesses continue to prioritize data security, the adoption of confidential computing is expected to rise.
This will likely lead to more innovations and improvements in the technology, making it more accessible and cost-effective for a wider range of businesses.
Additionally, as awareness grows, we can expect a richer ecosystem of support and services to develop, making implementation smoother and more integrated with existing IT infrastructures.
Conclusion
Now that you understand the importance and capabilities of confidential computing, it’s crucial to evaluate how it fits into your security strategy. Major cloud providers like AWS, Azure, and Google Cloud are implementing these technologies with various options for key management, allowing you to maintain control over your encryption keys. This is a pivotal feature, ensuring that you can leverage cloud computing resources while still enforcing rigorous data security policies.
Additionally, we are upgrading our data center infrastructure to support confidential computing, aiming to provide robust protections for your business data. Our team is ready to guide you through setting up and managing your confidential computing environment, ensuring you maximize your data security and compliance.
Let us help you navigate this advanced landscape of data protection, preparing your business not only for current security challenges but also for future technological advancements.