cybersecurity
Cybersecurity Hardening Services - Cloud Security Hardening
Protect Critical Systems and Cloud resources
What is the purpose of cybersecurity hardening services?
Cybersecurity Hardening limits the vulnerability of systems to attacks and therefore reduces their risk. It involves specific rules associated with hardening system configuration and a set of good practices.
Once systems, cloud resources or cloud tenants are hardened, their cybersecurity risk level has been decreased and the surface of attack reduced, hence security monitoring becomes more effective.
“For the past ten years, companies have been migrating their IT systems to the cloud. 93% of them now use it” (Microsoft).
“In the face of attacks, the cloud is not infallible. The massive use of telework has weakened the IT security of organizations. In 2020, at the height of the pandemic, 47% of businesses saw an increase in cyberattacks” (Thales).
Users are 99% responsible for cloud cybersecurity breaches (Gartner). Adopting a Cybersecurity Hardening approach helps create a secure computing environment.
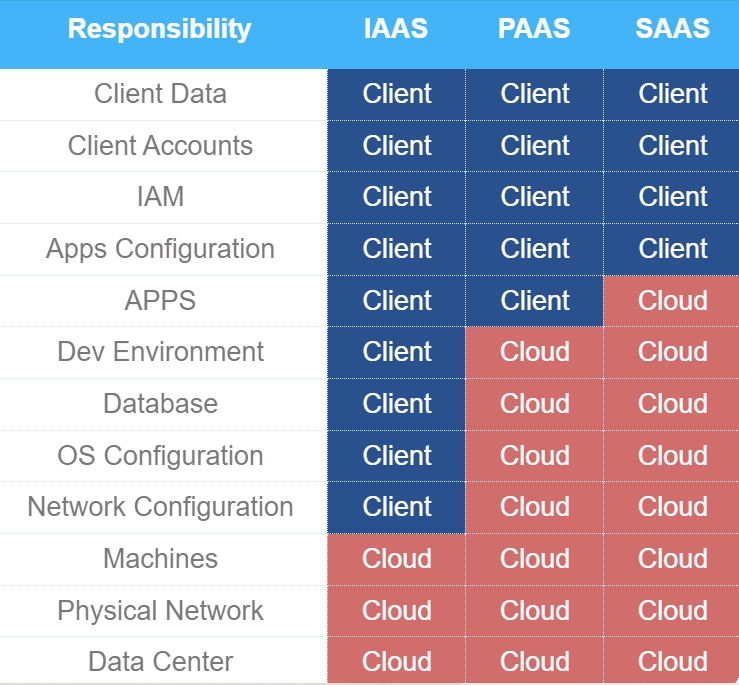
Cybersecurity Hardening Services
The first layer in the cybersecurity model
Preventive Services
Risk management, procedures, compliance and system hardening and protection services.
Detective Services
24x7 advanced monitoring and real time detection based on sophisticated anomaly detection.
Response Services
Isolate attacks and respond to threats in order to protect operations and maintain business uptime
Risk identification - the first step to cloud security hardening
- Microsoft 365
- Google Workspace
- Google Cloud Platform
- Microsoft Azure
- AWS
- Oracle Cloud Infrastructure – OCI
What does Cybersecurity Hardening involve?
Cybersecurity hardening should be carried out by trained and experienced engineers in system hardening. It involves going through an exhaustive list of controls and changing core system configurations. It is therefore essential to carefully study the use of the services before applying the hardening configurations. If this is not done properly, it is possible that the configurations affect functional services and interrupt them.
Exeo guides its customers through this process and implements a methodology based on system hardening best practices and vendor recommendations. The cybersecurity system hardening workflow is as follows:
- Audit of the systems to be hardened and generation of a gap analysis.
- Generate a detailed report which will categorise the controls to be hardened by level of criticality.
- Obtain the Client’s approval for each control to be hardened during an arbitrage session;
- Implement system hardening based on the recommendations of the report and the approval of the client.
Cloud security hardening
We believe that Cloud is more secure than other environments because it relies on a strong underlying infrastructure which is more secure than most of the on premise environments built in the enterprise. Furthermore, cloud environments incorporate all the necessary security technologies in order to operate safely and securely.
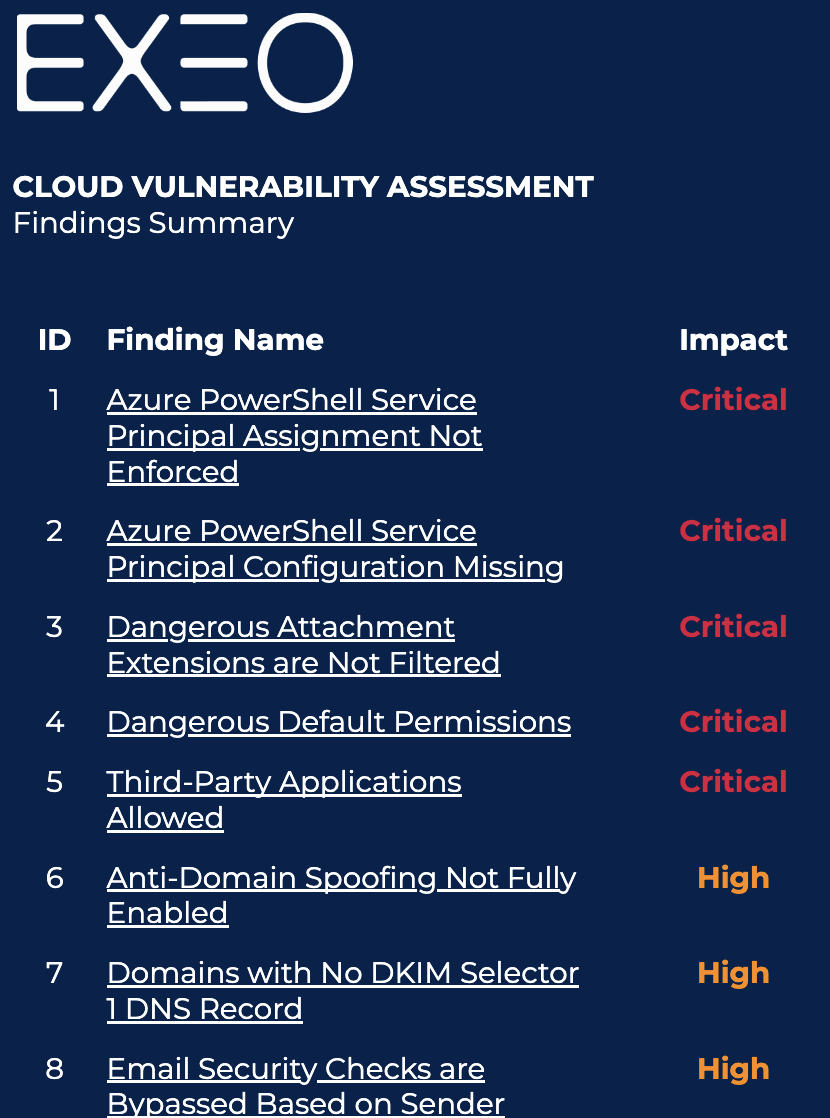
It is the cloud provider’s responsibility to secure the underlying infrastructure (data center, network, hardware & hypervisor), however it is the client’s responsibility to secure the environment he is leasing.
In this shared responsibility model, the responsibility is devided between the client and the cloud provider, the following illustration explains it in more details for three types of services (IAAS, PAAS & SAAS)
The Shared Responsibility Model
How does EXEO harden cybersecurity and cloud?
Part of the cybersecurity services EXEO provides is to harden the client environment in order to maximize the security of the hosted services and minimize the possibility of threats.
We have built our cloud hardening procedures based on the Common Internet Security (CIS) benchmarks and controls and different standards like ISO 27001, HIPAA or PCI-DSS.
Based on these industry leading security recommendations, we maintain predefined checklists of controls and have developed our own standard operating procedures in order to perform the security hardening
Hardening the environment also makes monitoring more effective at detecting threats, by focusing on the incidents that require attention. If you would like to know more about how we help our clients stay secure, you can also check our managed security service page.
Cybersecurity Hardening services standards and best practices
The system hardening exercise consists of reducing unused functionalities and closing unnecessary access. Hence, it should be prepared and performed with great care.
Cloud functionalities are enriched by providers on a regular basis. May of these functionalities are enabled by default while clients might not them and resulting in open vulnerabilities which are unknown to the the client.
In order to properly cover the entire scope of hardening, we have compiled a methodology based on the following recommendations:
- Those of the manufacturer by following all the functionalities
- Those of the Center for Internet Security
- Those of the standards like ISO 27001, HIPAA or PCI-DSS
- The Cloud Security Alliance’s Cloud Control Matrix
Through 2025, 99% of cloud security failures will be the customer’s fault.
Is the Cloud SecureGartner
Systems that we harden
Cloud Security Hardening Services
Cloud Productivity Suites
- Accounts security
- Email Deliverability, Spoofing protection
- Logs and alerts
- Sharing policies
- Data leakage
- Accounts security
- Email Deliverability, Spoofing protection
- Threat Protection
Cloud Platforms
- Identity & Access Management (IAM)
- Security Center
- Storage Accounts
- Database Services
- Logging & Monitoring
- Networking
- Virtual Machines
- Appservice
- Identity & Access Management (IAM)
- Logging & Monitoring
- Networking
- Virtual Machines
- Storage
- Cloud SQL Database Services
- BigQuery
- Identity and Access Management
- Networking
- Logging & Monitoring
- Storage
- Infrastructure Container Engine for Kubernetes (OKE)
500 security controls.
300 security controls
Database Platforms
- Surface area reduction
- Authentication & Authorization
- Password Policies
- Auditing & Logging
- Application Development
- Encryption
- Operating System Level Configuration
- Installation and Planning
- File System Permissions
- MySQL Permissions
- Auditing and Logging
- Authentication
Network - Replication
- Installation and Patches
- Directory and File Permissions
- Logging Monitoring And Auditing
- User Access and Authorization
- Connection and Login
- PostgreSQL Settings
- Replication
- Special Configuration Considerations

Cloud Hardening : 5 tips to Secure the Cloud
Cloud Hardening limits the vulnerability of the cloud to attacks. It involves specific rules regarding system configuration and a set of good practices.
cybersecurity risk assessment
BOOK A CLOUD AUDIT